The trial of a cybercriminal takes an unexpected turn: ZATAZ discovers that the site he once ran now redirects to an online scam.
The U.S. Department of Justice has confirmed the guilt of 33-year-old Liridon Masurica for operating the BlackDB forum [ZATAZ does not display the full URL, for reasons explained below], active from 2018 to 2025. This underground site sold stolen credentials, banking data, and server access used in tax fraud and identity theft schemes. Arrested in December 2024 and extradited to the United States, Masurica faces up to ten years in prison. Yet the trial revealed an unforeseen consequence: ZATAZ discovered that the forum’s URL, cited in official documents, is still active and now serves as a vehicle for a cyberattack. The domain, turned into a trap, silently redirects visitors into an attack they won’t see coming.
A landmark cybercrime trial
Liridon Masurica, a 33-year-old Kosovar national, has been found guilty by U.S. justice for administering the BlackDB forum. Between 2018 and 2025, this underground platform offered a full catalog of compromised data: online accounts, server credentials, and credit card numbers. Such information fueled a variety of frauds, including fake tax filings and identity theft.
His arrest in December 2024 marked the end of an international manhunt. Extradited to the United States, Masurica now awaits sentencing, facing a maximum of ten years in prison. The case once again highlights international cooperation between intelligence services and cybersecurity agencies in dismantling structured players in the digital black market.
A site turned into a digital trap
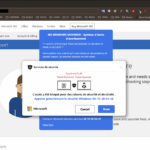
The case could have ended with a court ruling. Instead, the Justice Department’s official publication unexpectedly revived visibility for the BlackDB forum, whose address was cited in the court documents. But the domain did not disappear. ZATAZ found that the page, far from inactive, now redirects visitors to a well-known online scam.
Testing the URL, ZATAZ identified a “scareware” scheme, known as the “Microsoft virus alert.” The trick relies on a fake system notification displaying an alarming warning. The user is urged either to download a supposed security tool or to contact fake technical support. Both paths are designed to trap the victim, leading to malware installation or theft of banking data.
This shift illustrates the frequent recycling of cybercriminal infrastructure. Seized or abandoned domains can be quickly re-registered and reused for new frauds, benefiting from their past notoriety and residual traffic generated by media coverage.
A chain of institutional risks
The irony is that the Department of Justice, by citing the forum’s address in its official releases, indirectly contributes to spreading the trap. A curious citizen, journalist, or researcher clicking the link is now exposed to a scam attempt.
This scenario highlights the need for judicial and media authorities to check the status of domains cited in public decisions. Without precautions, a simple reproduction of a URL can become a gateway to an attack. This issue is not isolated: past investigations have shown that domains seized during criminal proceedings have been repurchased by new malicious actors.
Intelligence services and CERT teams (Computer Emergency Response Teams) emphasize the importance of monitoring the life cycle of domains tied to organized crime. Cybersecurity does not end with the arrest of an individual: it requires ongoing technical tracking of the digital footprints left behind.
The Masurica case illustrates both the judicial and technical dimensions of cybercrime investigations. Taking down an individual is not enough if the digital ecosystem they leave behind remains exploitable. The question now is how authorities can prevent their own publications from becoming amplifiers for new scams.